Difference Between Authentication And Authorization | Definition | Table..
We explain that what is the difference between authentication and authorization? With definition and comparison table. The differences between authentication and authorization are by definition, the focus of action, the order of priority, the process and the use. These words are often misinterpreted as synonyms. But they have different meanings in the technical world. These parameters are used to better understand both the words and the fair use.
Authorization is defined as the granting of an official permit or approval. This word was first coined between 1600-10. The word “authorization” is derived from the word “authorize”. The word ‘authorize’ originated from two medieval Latin words ‘auctor’ and ‘auctorizare’, an old French word ‘autoriser’ and the English word ‘author’. The root of the word “authorization” is “authorize.” ‘Authorize’ has its origin in the Latin word ‘auctor’, which means ‘the one who causes’.
Authentication is defined as a process to prove that something is genuine. The word “authentication” is derived from the word “authenticate”. The word “authenticate” is derived from the ancient Greek word “authentikos” and the late Latin word “authenticus.” The word “authentication” was first coined in the 1650s.
Let’s understand the use of the word “authorization.” Authorization means allowing a certain job to be done. For example, “Prince George gave you a signed authorization for consultation.” The phrase means that Prince George has allowed to investigate. Generally, the authorization has legal significance.
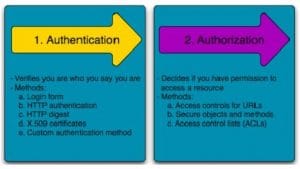 Now let’s understand the use of the word ‘authentication’. Authentication is a process to prove that a certain entity is valid. For example, “access to the system requires authentication.” The sentence means that participants who sign up to use the system must verify their identities.
Now let’s understand the use of the word ‘authentication’. Authentication is a process to prove that a certain entity is valid. For example, “access to the system requires authentication.” The sentence means that participants who sign up to use the system must verify their identities.
Comparison table between authorization and authentication (in tabular form)
Comparison Authorization Authentication Parameters
| Definition | Authorization determines whether the user can access the resource or not | Authentication means to identify the validity of the user |
| Getting closer | Determines whether the user has permission to access the resource or not. | Determines if the user is the same as it claims to be |
| Priority | Authorization is always the top priority | Authentication always comes after successful authorization |
| Process | The authorization process consists of verifying the user’s eligibility to access the system. | The authentication process consists of verifying the user’s assertions |
| Use | The word is used mainly in the technical and legal field. | The word is used mainly in the technical and legal field. |
| Example | The business owner is authorized to use our data for security purposes. | Joe was rejected because he failed the authentication process. |
What is authorization?
Authorization is a security mechanism that decides whether or not to allow greater access to the system. The system can be a file, a database, a service, a computer application, or computer software.
The first step for the web security system is authentication. These steps grant or deny permission to the user. Only if this step is successful can the user continue to use the system.
There are four main types of authorization in API.
- API key
- Basic authentication
- HMAC (hash-based message authorization code)
- OAuth
Hash-based message authorization code (HMAC) is very advanced. HMAC uses a secret key that only the user and the server know.
There are two types of OAuth.
- Single Leg OAuth
- Two-legged OAuth
One-way OAuth is used when data is not highly confidential. This can be used when it is not very important to protect the data. It is used in the case of read-only information.
Three-way OAuth is used when data is highly sensitive. It is used when it is extremely important to protect data. Three groups that participate in this type of authorization are:
- The authentication server
- The resource server (API server)
- The user or the application
What is authentication?
Authorization is the process that verifies the claims made by the user about their identity. Work to secure the system. Authentication kicks in only after authorization has been successfully completed.
The application program interface (API) is a set of certain rules and protocols that must be followed to design any software application. Authentication is used to secure a modern and advanced system. They are used to prevent any illegal use of data.
There are five main types of authentication.
- Password based authentication
- Multi-factor authentication
- Token-based authentication
- Certificate-based authentication
- Biometric authentication
Biometric authentication is further classified as:
- Facial recognition
- Voice identifier
- Eye scanner
- Fingerprint scanner
Authentication is a way to ensure the security of the system and user data. Their goal is to keep the system safe and private. Hackers always find a new way to enter the system and leak information. Therefore, the basis for authentication should improve over time. A good authentication system is key to creating effective and durable application software. Biometric authentication is the latest and most reliable type of authentication. Among the different types of biometric authentication, a fingerprint scanner is the most widely used.
Key differences between Authorization and authentication
- Authorization is the process of specifying rights related to a particular system. Authentication is a process that involves user verification.
- Authorization validates the user’s privileges, but authentications verify their credentials.
- Authorization takes precedence over authentication.
- Authorization asks what permission the user has to access the system. Authentication verifies whether the user is legitimate or not.
- Authorization verifies the role of the user and the access right. Authentication requires username and password.
Final Thought
Authorization and authentication go hand in hand. Both have the same importance but have different priority. It is important to check whether the user has permission or not. It is equally important to verify the claims made by the user about their identity. Authorization and authentication are very important to software developers. It is a way of guaranteeing the security and privacy of the data.
